top of page
Posts


AWS Security Architecture Crash Course
In AWS, security view starts with how accounts are managed. AWS uses a multi-account setup to keep services and workloads separated, making it easier to manage resources safely. Organization: A way to manage multiple AWS accounts together from one place. Account: An isolated space within an organization, with its own resources, billing, and permissions, helping to separate different tasks and responsibilities. When building an efficient AWS organization, it's important to und

RNREDDY
Nov 26, 20253 min read


End-to-End Encryption on Amazon EKS with cert-manager
End-to-End Encryption on Amazon EKS with cert-manager Organizations handling sensitive applications demands secure communications that ensure data privacy, even between internal services. However, Some of the valid challenges I see: Managing certificates for each microservice is complex. Kubernetes ingress with Network Load Balancer doesn't support client certificates. Manual certificate rotation increases administrative effort. Mutual TLS is not achievable with standard Kube

RNREDDY
Nov 26, 20251 min read


AWS Lambda Integration Patterns with SQS and SNS
Did you know that AWS once used shipping containers to speed up data transfers? In 2009, they launched "AWS Import/Export," allowing customers to physically send storage devices to AWS data centers, bypassing the internet for faster massive data uploads. Love or hate this intro? Hit reply and tell us why! In this issue : AWS Lambda Integration Patterns with SQS and SNS CloudBees Acquires Launchable to Boost Iterative Development Usage of AI Rapidly Expands Once DevOps Teams A

RNREDDY
Nov 26, 20253 min read


AWS Security Groups Common Error Codes and Resolutions
When I started my cloud career a decade ago, the most frequent and helpless scenarios were often caused by security group mess-ups. These misconfigurations can cause issues from server inaccessibility to security breaches, so correct security group configuration is essential for a secure, functional cloud environment. Here, I provide a breakdown of common error codes related to security groups, along with their contexts and solutions: Security Groups Tips and Tricks: Use spec

RNREDDY
Nov 26, 20251 min read

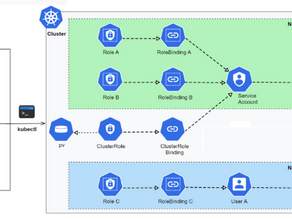
Understanding Kubernetes RBAC
Understanding Kubernetes RBAC Some of you may already know this. Let's quickly revise how RBAC works. Step 1: Define Roles (Role or ClusterRole): What actions are allowed within a namespace (Role) or across the entire cluster (ClusterRole). Step 2: Creating Service Accounts or Users/Groups: Set up service accounts within Kubernetes or manage external users/groups to take on these roles. Step 3: Bind Roles to Accounts, Users, or Groups: Use RoleBindings to connect roles to ser

RNREDDY
Nov 26, 20252 min read

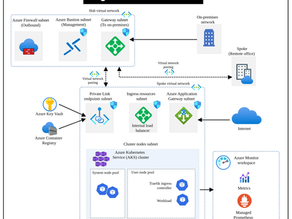
How to Design Azure Kubernetes Service (AKS) Cluster
How to Design Azure Kubernetes Service (AKS) Cluster Before you design an Azure Kubernetes Service cluster, it helps to step back and understand how Kubernetes itself is structured. At its core, Kubernetes separates responsibilities between the control plane and the worker nodes. The control plane hosts the API server, scheduler, controller manager, and etcd. These components maintain the desired state of the cluster and make decisions on scheduling, orchestration, and cluste

RNREDDY
Nov 26, 20253 min read


CRI-O vs Containerd
CRI-O vs Containerd: Undersanding Kubernetes Container Runtimes When your Pod starts in Kubernetes, the container runtime is one of the first components to take action. What Is a Container Runtime? A container runtime is the system level component responsible for: Pulling container images from a registry Unpacking and mounting the image layers Creating isolated environments using Linux namespaces and cgroups Executing the container process using a low level runtime like runc

RNREDDY
Nov 26, 20254 min read


Kata vs Traditional Containers
Kata vs Traditional Containers Kata Containers is now one of the leading methods for running containers inside isolated virtual machines. What are Kata Containers? Kata Containers perform like containers, but provide the workload isolation and security advantages of VMs. It combines the benefits of containers and VMs. The project is managed by the OpenStack Foundation. With Kata, you can implement VM isolation at the container level and container isolation using hardware virt

RNREDDY
Nov 26, 20252 min read
Designing Effective Architecture to Bypass API Gateway Payload Limits
API gateways play a crucial role in managing and securing traffic between clients and backend services. However, many API gateways impose payload size limits that can hinder applications needing to send or receive large amounts of data in a single request. When payloads exceed these limits, requests fail, causing disruptions and poor user experience. Designing an architecture that overcomes these payload restrictions is essential for building scalable, reliable APIs. This pos

RNREDDY
Nov 18, 20253 min read


Unveiling RnReddy's Technological Perspectives
Technology is evolving at a breakneck speed, and keeping up with the latest trends and best practices can sometimes feel overwhelming. Over the years, I have immersed myself in the world of DevOps, Kubernetes, and OpenShift administration, and I’m excited to share some of the most valuable insights I’ve gathered. Whether you’re a developer, system administrator, or DevOps engineer, this post aims to provide practical knowledge and actionable tips that you can apply right away

RNREDDY
Nov 18, 20253 min read


Kubernetes Upgrades - How Not to Mess Up?
Kubernetes Upgrades - How Not to Mess Up? You may have heard about the Reddit Kubernetes upgrade horror story, a 314 minute outage caused...

RNREDDY
Sep 11, 20252 min read


Improving Kubernetes Latency with External Traffic Policy and Session Affinity
Improving Kubernetes Latency with External Traffic Policy and Session Affinity When dealing with Kubernetes Services, achieving optimal...

RNREDDY
Sep 11, 20252 min read


Why Did My Kubernetes Pod Stop Abruptly?
Why Did My Kubernetes Pod Stop Abruptly? We’ve all been there. Your Pod is running along, doing its job, and then suddenly - it stops. No...

RNREDDY
Sep 10, 20252 min read


Why Should You Design Pods for Stateless Applications?
Why Should You Design Pods for Stateless Applications? Yes, you can run stateful workloads in a Kubernetes pod. But it’s not the...

RNREDDY
Sep 10, 20252 min read


Autoscaling - HPA vs VPA vs KEDA
Kubernetes Autoscaling - HPA vs VPA vs KEDA Which type of autoscaling should I use for my workload? Can I scale based on message queues...

RNREDDY
Sep 10, 20252 min read


Kubernetes Patterns - Part 2
Init Container, Sidecar, Ambassador, Adapter, Controller, Operator Let’s look into a few more crucial patterns every Kubernetes...

RNREDDY
Sep 10, 20252 min read


OOMKilled and ImagePullBackOff Simplified
Kubernetes OOMKilled and ImagePullBackOff Simplified Today's use case is about OOMKilled and ImagePullBackOff. Let's take a quick look at...

RNREDDY
Sep 10, 20252 min read


Cloud Controller Manager Chicken and Egg Problem
Kubernetes Cloud Controller Manager Chicken and Egg Problem In Kubernetes, there's a lesser known yet frustrating bootstrap paradox - the...

RNREDDY
Sep 10, 20253 min read


Kubernetes Security Must Practices
Kubernetes Security Must Practices You know there are tons of content on Kubernetes Security Best practices, the moment it is conceived...

RNREDDY
Sep 10, 20252 min read


Kubernetes Patterns - Part 1
Kubernetes Patterns - Part 1 If you've been working with Kubernetes for a while, you know it’s more than just running containers. We...

RNREDDY
Sep 10, 20253 min read
bottom of page